The latest Cisco ISE install involved migrating the customer from ACS 5.8 to ISE 2.3. They already had several authorization rules configured (over 50) in ACS so the ACS to ISE 2.3 migration tool was downloaded from Cisco. If you’ve never used it before, it is very easy to use and simplifies the migration. The biggest thing to remember is that you only use it on a fresh install of ISE. I’ve used previous versions and this is the first time I’ve had an issue like this occur.
The export from ACS and subsequent import into ISE appeared to go smoothly. It took less than 30 minutes to do all the steps using the migration tool. After the import was complete, I had the customer log into the ISE node in order to join it to Active Directory. The join point was already created because it was imported from ACS. The customer then went to the Groups tab and that’s when we noticed that the SID values for all of the groups were set to the same value as the Group name. No big deal. We’ll just click the “Update SID values” button and clear that up.
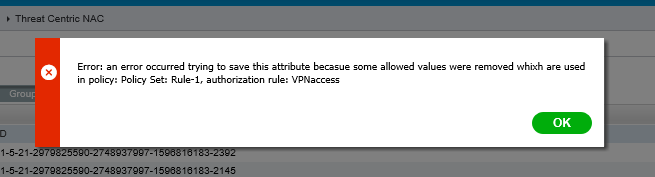
Clicking the update button pulled all the right SID values from AD and assigned them to the respective group. When the customer clicked the Save button, they received the following error:
Error: an error occurred trying to save this attribute becasue some allowed values were removed whixh are used in policy: Policy Set: Rule-1, authorization rule: VPNaccess
Yes, the misspelled words are exactly how they were in the error message.
We tried changing a single SID to the correct SID and it would give the same error. We tried various things like resetting the rule and manually configuring the AD group used but nothing worked. The customer even opened a TAC ticket. The TAC engineer suggested editing the policy rule to remove the AD group condition or deleting the rule all together. Either one would in turn allow them to update the SID values successfully. Panic started setting in because the customer was not happy at the thought of having to delete the rules and then have to manually recreate over 50 authorization rules. Editing that many rules to remove the AD group condition and then add them back after updating the SID values wasn’t a good option, either.
After a little more thought (and a lot of coffee), a possible solution hit me. They still had the ACS to ISE migration tool on their desktop with the exported data. So we tried the following:
- Delete the RADIUS and Device Admin policy sets.
- Update the SID values for the AD groups in ISE.
- Successfully saved since there were no policy rule conflicts.
- Enabled ACS to ISE migration in the ISE node CLI.
- Run the ACS to ISE migration tool again.
- No export from ACS required because the original export was still there.
- Only Policy Elements and Access Policies were checked for import.
- Disabled the ACS to ISE migration from the ISE node CLI.
We doubled checked that the AD group SID values weren’t affected (they weren’t) and verified the policy sets imported correct. We were then able to verify that TACACS+ authentications and authorizations occurred correctly using the imported policy set and a test switch. RADIUS authentications, which only accounted for 2 rules, also worked properly.
same here. It fixed it as per the post!!!
You are the man.
please from your own experinece, can you itemise the steps needed to migrate from ACS 5.8 to any latest version of ISE ?
You can find a really well written guide on the Cisco Communities site. It covers pretty much everything I’ve come across outside of what I wrote in this post.
https://community.cisco.com/t5/security-documents/how-to-migrate-acs-5-x-to-ise-2-x/ta-p/3635997