It’s a scenario I’ve seen pretty often. You try to log into the CLI of an ISE node (SSH or console) with the admin account and the login fails. You verify that the password is correct. The problem is that you’ve been locked out due to too many failed logins. Unfortunately, the only solution you have is to reboot the node using an installation ISO and go through a password recovery. It’s not a difficult process but it does require downtime for that node.
I have seen this more often than not caused by security scanners. Businesses like to test their systems for vulnerabilities. The ISE node isn’t excluded from the scan and a brute force attempt is made by the scanner to log into the node using an SSH session. This causes the CLI admin account to become locked. If they had utilized a second (or even third) CLI admin account, they could have logged in and reset the default admin account.
The process for adding additional CLI logins is simple. Log into the ISE node CLI and run the following commands:
configure terminal
username <new user> password plain <password> role adminIt’s important to add role admin to the end. If you put role user, the account you create will have restricted access to CLI commands (ie no configuration commands). Be sure to test your new user account before you actually need it.
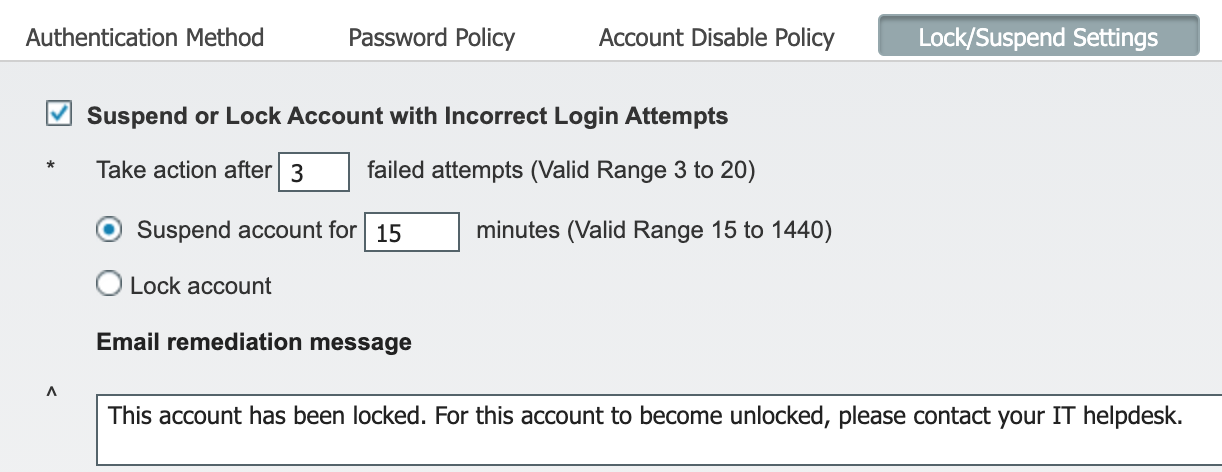
Update: The above information about the account being locked was for cases where the “Lock/Suspend Settings” for admin accounts was set to lock the account. If you set it to suspend for X amount of minutes (15 to 1440), the account will unlock after the specified amount of time.
Smart! That’s for the tip.
so you need to inform compliance team that you created a new user and they will add that user to their scans. What do you win with that? do you plan to not tell them about all the users on the infrastructure? Thats not exactly clever. better would be if the accounts recover from this state automatically – whats the point of locking forever?
also, forcing your users to write in all capital letters is really really annoying.
Yes, you could inform the compliance team. It also goes with someone that runs automated attacks using common names like “Admin” or “Administrator” in order to prevent lock outs.
“also, forcing your users to write in all capital letters is really really annoying.”
100% agree. I didn’t even realize this was happening. Not sure if it’s my theme or a plugin causing this. Thank you for bringing it to my attention.
Update: It was the theme I was using. I’ve changed to a different theme that doesn’t force comments to be in all caps. I have also updated the article since I did not mention this was for cases where the “Lock/Suspend Settings” was set to lock the account.
Awesome tip Brad. Thanks for sharing this.