Joining nodes to a Cisco ISE deployment requires the admin nodes to trust the SSL certificate on the new node. The SSL certificate that must be trusted is the one used for the Admin portal. Self-signed or private certificates (e.g. local enterprise CA) are desired for the Admin portal because of the way BYOD works when using the ISE server as a CA. Why? Using 3rd party certificates for the admin portal requires the ISE node to be a subordinate CA to the root CA so the ISE node can issue certificates for BYOD. This isn’t an option with public CA’s like GoDaddy.
Cisco ISE releases before 2.3 required the admin node to have one of two configuration in place before joining the new node:
1. The root CA certificate that issued the new node’s SSL certificate must be in the Trusted Certificates store on the admin node or
2. The self-signed certificate from the new node must be exported from the new node and imported into the admin node’s Trusted Certificates store.
Option number 2 is an extra step that doesn’t take a lot of time but it is still an extra step. Cisco ISE 2.3 removes that requirement. Now, when you go to join a node to a deployment that is using a self-signed certificate that isn’t already trusted, you have the option to import the certificate automatically.
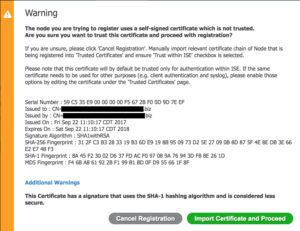
Importing the certificate will automatically place it into the PAN Trusted Certificates store.
Note: If you are using a self-signed certificate, I only recommend using it for the Admin portal. All other uses, especially EAP authentication, should use a trusted certificate. This is so endpoints don’t throw an error when connecting to the ISE node for the guest portal and EAP authentication.