Steps to authenticate VPN users connecting to Meraki MX VPN.
Configuring the Meraki MX VPN client
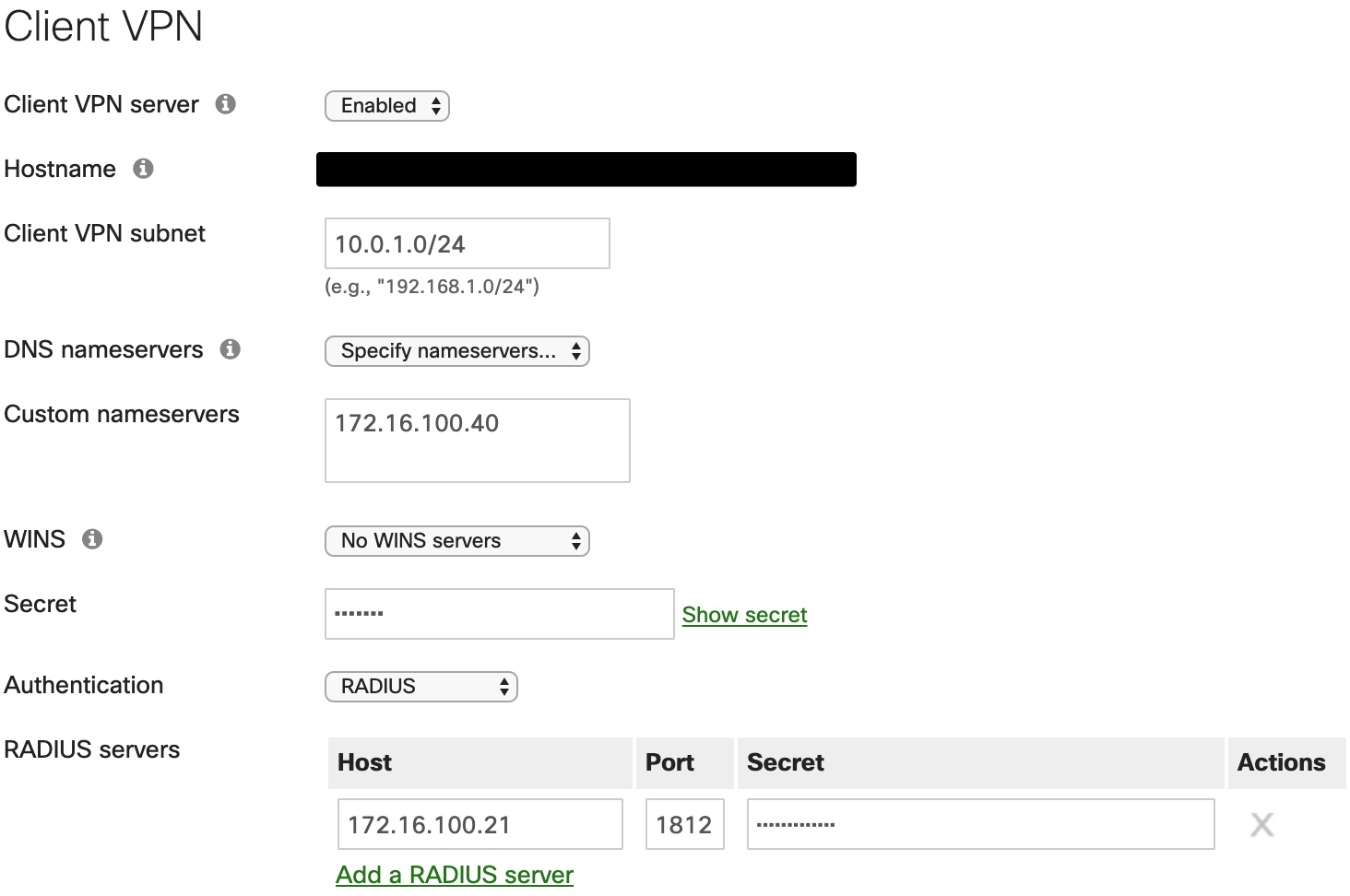
- Go to your Meraki dashboard and navigate to Security & SD-WAN > Configure > Client VPN.
- Configure the settings for your environment.
- Enable the Client VPN Server.
- Client VPN Subnet: Any valid subnet with enough IP addresses to handle the number of clients. I would avoid LAN overlap.
- DNS Nameservers: Point to local LAN DNS servers if clients require access to local LAN resources by FQDN.
- Secret: This is the secret/password used to establish the VPN tunnel. This is not the RADIUS shared secret.
- Authentication: Set to RADIUS.
- If no RADIUS servers are configured, you can add a RADIUS server here.
- The default authentication port is 1812.
Configure ISE for MX VPN authentication
- Add the MX device as a Network Access Device (NAD) in ISE.
- Administration > Network Resources > Network Devices > Add
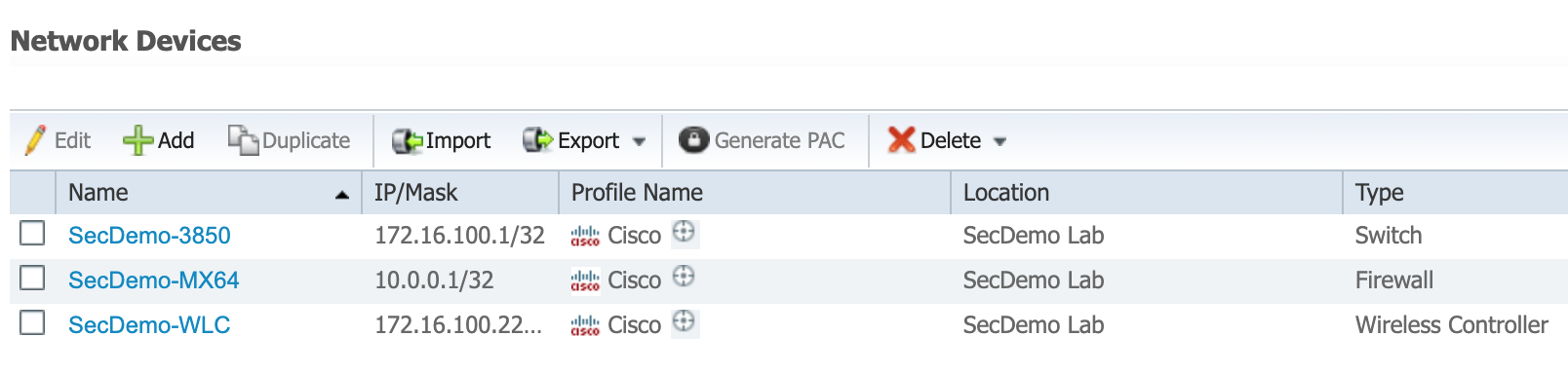
- Use the management LAN IP of the MX.
- For this example, I created a Network Device Group called Firewalls. The MX64 was added to this group.
- Make sure to use the same RADIUS secret here as you did in the RADIUS server configuration on the Meraki dashboard.
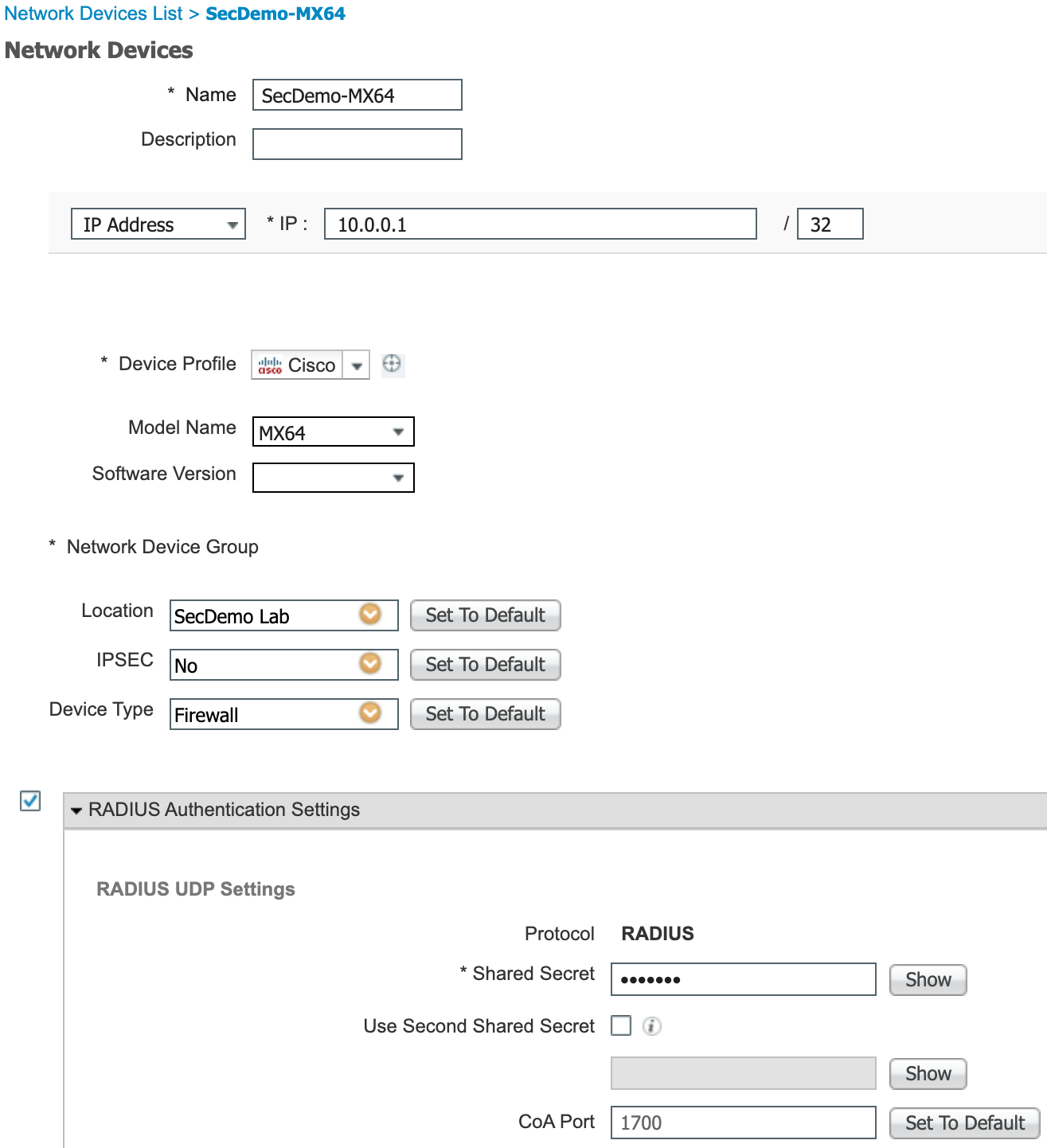
- Administration > Network Resources > Network Devices > Add
- Create the Policy Set to use for client authentication and authorization.
- Policy > Policy Sets > Click the plus (+) sign in the top-left
- The conditions for the policy set are:
DEVICE·Device Type Equals All Device Types#Firewall
Radius·Framed-Protocol Equals PPP - This example is using Default Network Access for the Allowed Protocols. You can narrow it down to a custom protocol list that only includes PAP_ASCII.
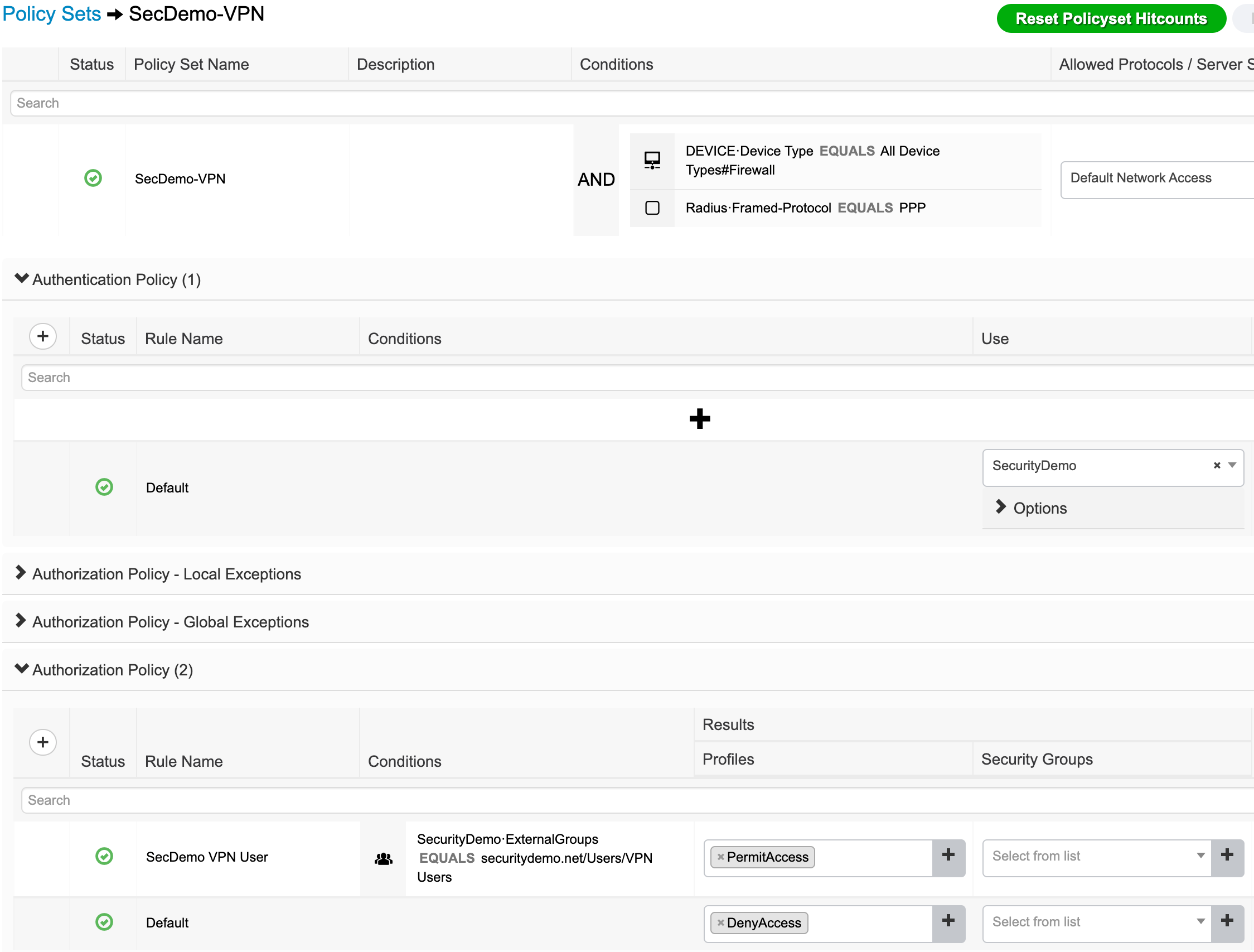
- Modify authentication and authorization settings.
- Authentication: I am using AD to authenticate the users so only the SecDemo AD join is being used. The AD user group was added under Administration > Identity Management > External Identity Sources > Active Directory > [AD Join] > Groups.
- Authorization: Only user accounts belonging to the VPN Users AD group are permitted access. All others are denied access.
Configure your client and test
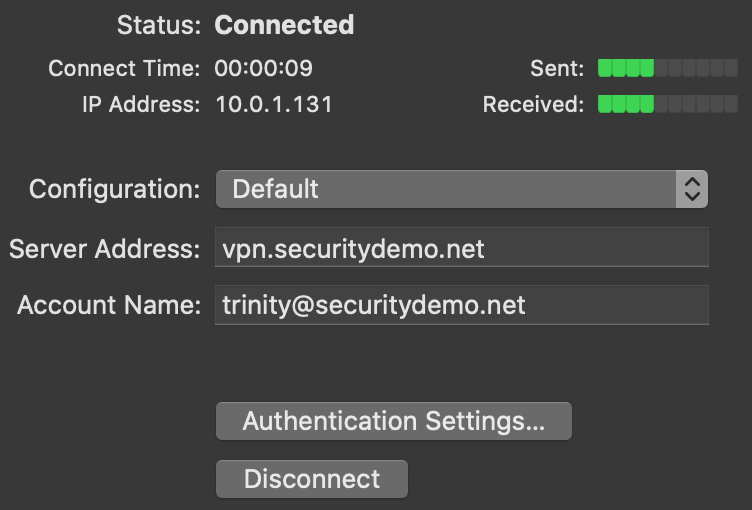
At this time, the Meraki VPN only supports L2TP over IPsec for client authentication. You can find a full list of client configuration steps on the Meraki Client VPN OS Configuration site. I used the Mac OS configuration for my lab test.
The first user account I tested (screenshot above) was successful because they belong to the VPN Users AD group. The user account that failed did not belong to the correct AD group.

Note that the Endpoint ID will always show CLIENTVPN.