Sending authentications to different RADIUS servers/deployments has been pretty easy for wireless controllers for a long time now. Configure the RADIUS servers and assign them per SSID/WLAN. This wasn’t always possible for wired users on the same switch. With IBNS 2.0, we can now utilize policy maps to configure each port to send the authentication to a different RADIUS server deployment.
This is not really an ISE specific configuration. This is 100% IBNS 2.0 on the switch.
The setup for this configuration is as follows:
- Cisco ISE 2.7p1 (172.16.100.21)
- PacketFence 10.0.1 (172.16.100.27)
- Cisco C3650 switch with IOS 16.6.8
- Windows 10 VM with PCI pass-through (physical network connection)
The configuration I’m using is based on my IBNS 2.0 template. I used the same template you can find on my NAD configuration templates page with the a few tweaks.
RADIUS Server configuration
Along with the RADIUS server configuration for ISE, I added the configuration for the PacketFence (PF) server and RADIUS server group:
radius server ISE
address ipv4 172.16.100.21 auth-port 1812 acct-port 1813
automate-tester username RADIUS-Test probe-on
key 7 [RADIUS secret]
aaa group server radius ISE-RADIUS
server name ISE
deadtime 15
radius server PacketFence
address ipv4 172.16.100.27 auth-port 1812 acct-port 1813
automate-tester username RADIUS-Test probe-on
key 7 [RADIUS secret]
aaa group server radius PF-RADIUS
server name PacketFence
deadtime 15 I also added both ISE and PacketFence to the dynamic author list:
aaa server radius dynamic-author
client 172.16.100.21 server-key 7 [RADIUS secret]
client 172.16.100.27 server-key 7 [RADIUS secret]AAA configuration
Once the RADIUS servers are configured, we need to create the AAA configuration. Normally with a single RADIUS server group you can use default as the method list name. Since we have two different RADIUS server groups, we need to give them distinct method list names. I’m using ISE-LIST and PF-LIST to designate which method is for the ISE RADIUS server group and which is for the PacketFence RADIUS server group.
aaa authentication dot1x ISE-LIST group ISE-RADIUS
aaa authorization network ISE-LIST group ISE-RADIUS
aaa accounting identity ISE-LIST start-stop group ISE-RADIUS
aaa accounting network ISE-LIST start-stop group ISE-RADIUS
aaa authentication dot1x PF-LIST group PF-RADIUS
aaa authorization network PF-LIST group PF-RADIUS
aaa accounting identity PF-LIST start-stop group PF-RADIUS
aaa accounting network PF-LIST start-stop group PF-RADIUSPolicy Map configuration
Here is where we start tying this all together. The policy map has an important change to designate where to send the AAA request. The authenticate using calls are configured with the method list name so that the port in which the policy map is tied to knows where to send the AAA request. So instead of authenticate using dot1x priority 10, for example, we need to tell it which method list to send the authentication (auth-c) and authorization (auth-z).
I’m pasting the relative sections where changes were made below. Note that each policy map includes the name of the RADIUS deployment so it’s easier to see which is which.
policy-map type control subscriber Dot1x-ISE
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x aaa authc-list ISE-LIST authz-list ISE-LIST priority 10
event authentication-failure match-first
5 class Dot1x_Failed do-until-failure
10 terminate dot1x
20 authenticate using mab aaa authc-list ISE-LIST authz-list ISE-LIST priority 20
...
30 class Dot1x_No-Resp do-until-failure
10 terminate dot1x
20 authenticate using mab aaa authc-list ISE-LIST authz-list ISE-LIST priority 20
...
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x aaa authc-list ISE-LIST authz-list ISE-LIST priority 10
policy-map type control subscriber Dot1x-PF
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x aaa authc-list PF-LIST authz-list PF-LIST priority 10
event authentication-failure match-first
5 class Dot1x_Failed do-until-failure
10 terminate dot1x
20 authenticate using mab aaa authc-list PF-LIST authz-list PF-LIST priority 20
...
30 class Dot1x_No-Resp do-until-failure
10 terminate dot1x
20 authenticate using mab aaa authc-list PF-LIST authz-list PF-LIST priority 20
...
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x aaa authc-list PF-LIST authz-list PF-LIST priority 10
Port template and port configuration
You can assign the policy map directly to the port but I’m using port templates (monitor mode in this example) on this switch. The service-policy command tells the switch which template to use. Each template has a descriptive name to make them easier to tell apart.
template Port-Dot1x-ISE
dot1x pae authenticator
switchport access vlan 100
switchport mode access
spanning-tree bpduguard enable
mab
subscriber aging inactivity-timer 60 probe
access-session host-mode multi-domain
access-session port-control auto
authentication periodic
authentication timer reauthenticate server
service-policy type control subscriber Dot1x-ISE
ip dhcp snooping limit rate 100
template Port-Dot1x-PF
dot1x pae authenticator
switchport access vlan 100
switchport mode access
spanning-tree bpduguard enable
mab
subscriber aging inactivity-timer 60 probe
access-session host-mode multi-domain
access-session port-control auto
authentication periodic
authentication timer reauthenticate server
service-policy type control subscriber Dot1x-PF
ip dhcp snooping limit rate 100I’m setting gigabit interface 1/0/1 to send authentications to ISE and interface 1/0/2 to send authentications to PacketFence.
interface GigabitEthernet1/0/1
source template Port-Dot1x-ISE
device-tracking attach-policy IP-Tracking
dot1x timeout tx-period 7
dot1x max-reauth-req 3
interface GigabitEthernet1/0/2
source template Port-Dot1x-PF
device-tracking attach-policy IP-Tracking
dot1x timeout tx-period 7
dot1x max-reauth-req 3We can see the configuration for each port by running the show run interface gi1/0/x and show derived-config int gi1/0/x (x=port number).
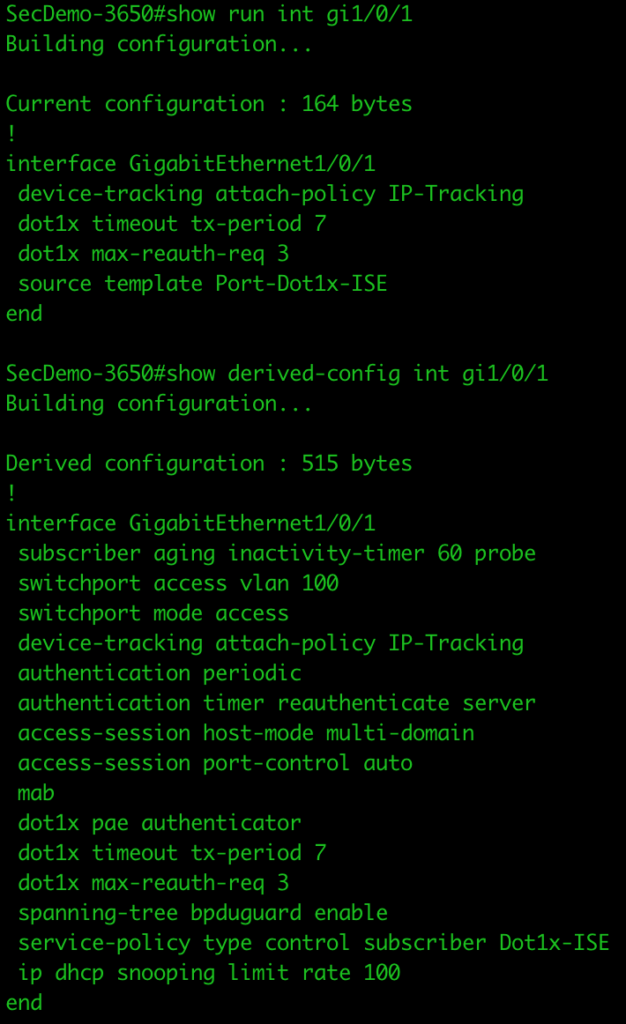
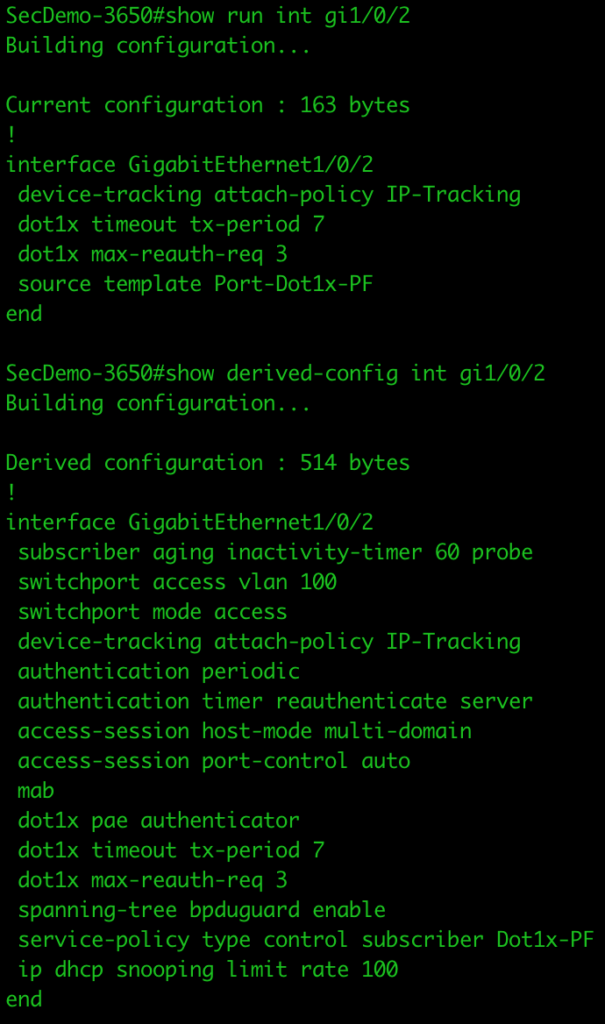
Testing the configuration
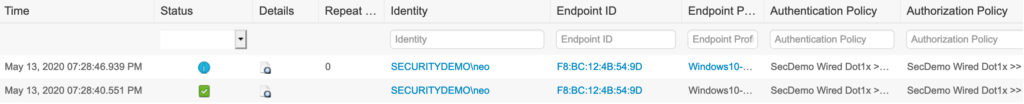
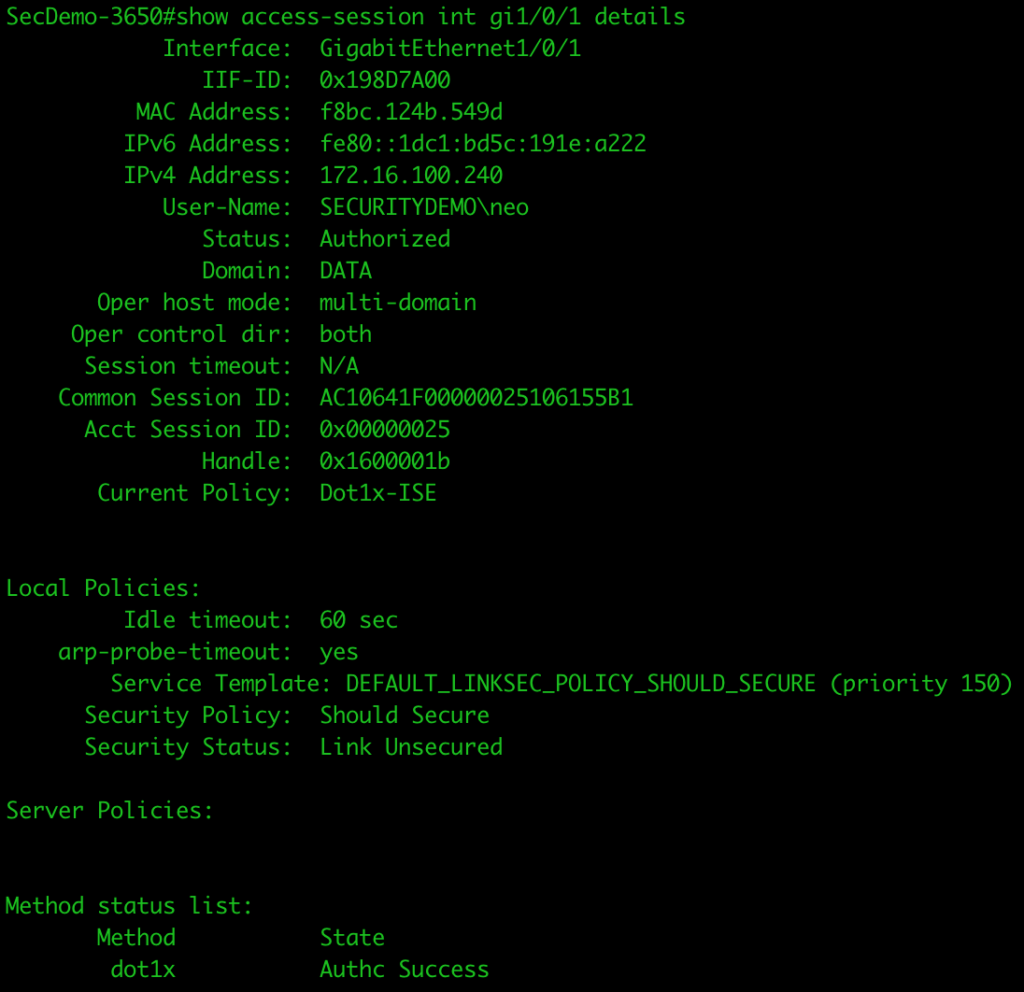
I first plugged the Windows 10 VM (configured for EAP-MSCHAPv2) into port gi1/0/1 and logged in with an AD user account. The result was a successful authentication on the ISE node.
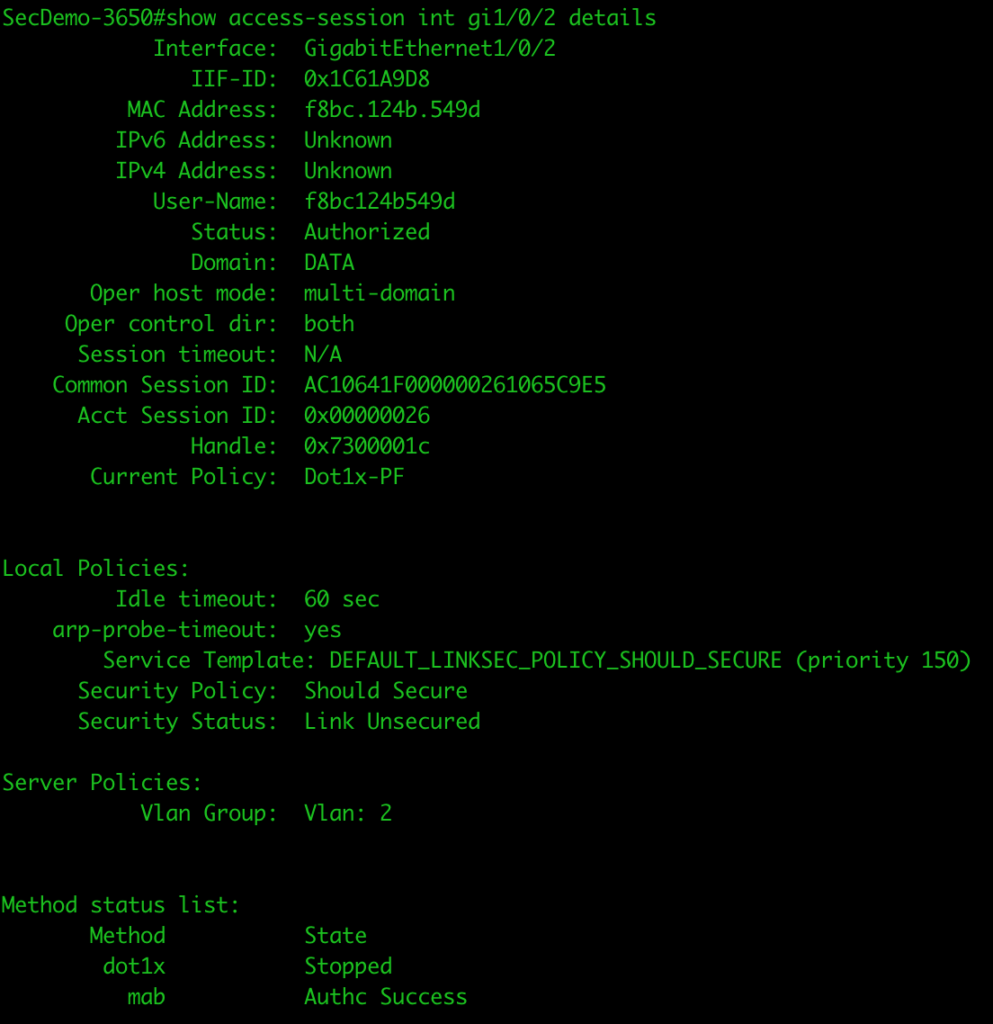
We can also see the access session on the switch port itself showing it is successful. The Current Policy shows it is using the correct policy map (Dot1x-ISE).
I logged off, moved the connection over to port gi1/0/2, and logged in again with the same AD user account. While the authentication was rejected (I need to work on my PacketFence configuration), we can still see that the authentication went to the PacketFence server.
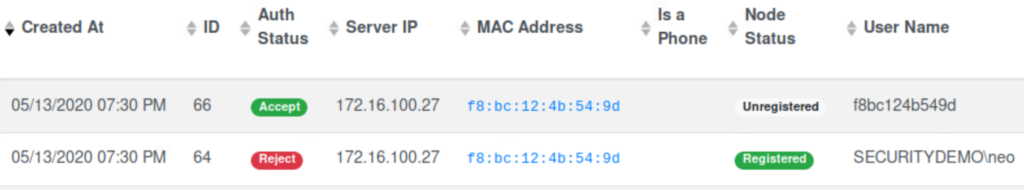
The access session on the port also shows that dot1x stopped, since it was rejected, but it fell through to MAB which was successful. The Current Policy shows it is using the correct policy map (Dot1x-PF).